Hospital security
Hanwha Vision, a pioneer in security and surveillance solutions, introduces the Audio Beacon, SPS-A100M, an advanced AI-powered audio surveillance solution that ensures users can be alerted and respond rapidly to critical situations. Equipped with a powerful 90dB speaker, five integrated microphones, and intelligent sound classification, the Audio Beacon is engineered to enhance situational awareness and real-time communication. Decision-making and direct communication LED ring provides a vi...
Athena Security, a pioneer in AI-driven physical security solutions, has announced the launch of its new Hospital Visitor Management System (VMS) on the Apple iPad. Purpose-built to meet the critical needs of healthcare facilities. Athena’s Hospital VMS is the first Apple iPad solution in the industry to offer seamless offline capabilities—ensuring that hospitals stay operational and secure, even amidst internet interruptions due to down servers, power outages, or natural disasters....
Hospitals have no peaceful nights, most of the time! During one such night, there was a chilling alert from the maternity ward: an infant's ankle tag had triggered an unauthorised exit alarm. Immediately, the hospital's integrated security system - unseen guardian - sprang to life. Doors around the nursery automatically locked down, surveillance cameras swiveled to cover every exit, and a live video feed, along with an alert, reached security personnel’s mobile devices – all in a fl...
Nearly two in five healthcare workers in the U.S. say they have considered leaving their positions due to safety concerns, with almost half (45%) likely to leave their job in the next 12 months, according to new research conducted by Verkada in partnership with The Harris Poll. Verkada's Healthcare Safety Report Against the backdrop of an already challenging environment that has pushed 138,000 nurses out of the workforce since 2022, Verkada's Healthcare Worker Safety Report...
The 17th Real Estate Development (RED) Summit – Saudi Arabia | Europe Edition, hosted by GBB Venture, turned the spotlight on Lisbon as it welcomed some of the most influential names from Saudi Arabia's evolving real estate sector for two days of purpose-driven exchange, global synergy, and fresh perspectives. Held at the iconic Lisbon Congress Centre's RIO Pavilion, the summit brought together key decision-makers from Saudi Arabia's rapidly evolving real estate sector and Europe's pionee...
Claroty, the cyber-physical systems (CPS) protection company, announces new capabilities in its SaaS-based Claroty xDome platform that provide organisations with an impact-centric view of their CPS environment. The new additions, Device Purpose and Risk Benchmarking, allow users to see how the overall risk of an environment is affected by the processes involved in a device’s use – as production lines, building floors, hospital wings, and more – and prioritise risk reduction ef...
News
iDenfy, a US-based fraud prevention and identity verification company best known for its AI-powered RegTech automation solutions, partners with Reppublika Data Analytics & Technologies, a pioneer European software firm providing innovative SaaS solutions to the market research industry. iDenfy’s identity verification software will help the business verify all customers who are conducting surveys online while detecting fraudulent users with fake personal details or other renderings, often used to bypass verification checks for fraudulent purposes. Enhanced trust and data quality The switch will help to validate the legit survey respondents who want to address market research problems Reppublika Data Analytics & Technologies, a top European software company with a focus on SaaS solutions for the market research industry, is partnering with iDenfy, a Lithuania-based platform that provides identity verification and fraud prevention. With the integration from iDenfy, the survey and research service provider will aim to boost conversions, streamlining all components of the Know Your Customer (KYC) flow, with the help of technologies like iDenfy’s 3D active liveness detection. The switch will help to validate the legit survey respondents who want to address market research problems. Together, Reppublika and iDenfy will work to provide a solution for the market research industry to combat fraud, ensure data quality, and enhance trust. Innovative solutions Reppublika Data Analytics & Technologies is known for their innovative SaaS solutions, which apply across the competitive landscape of panel management technology, survey platforms, and 360° media measurement technology serving clients, including market research agencies, publishers, media agencies, and Joint Industry Committees (JICs). However, in the past, Reppublika has dealt with complaints and concerns regarding fraud, particularly through the use of bots and fake respondent issues that not only distort survey data but also contravene established principles of validity and reliability related to survey data. Trusted identity partner iDenfy’s identity Verification and Reppublika’s panel management allows the company to validate the identity Reppublika decided to partner with iDenfy as its ID verification partner for several reasons, including its industry-leading technology, European-based company, and trustworthy anti-fraud compliance innovations for better-deterring users. iDenfy’s identity Verification and 3D Active Liveness products complement Reppublika’s panel management and surveying tools, allowing the company to validate the identity of respondents with almost unfathomable accuracy. These tools have allowed Reppublika’s clients, such as Talk Online Panel, to ensure that their survey data is based on real-life respondents. Real-time verification In an industry plagued by concerns regarding bots and fraudulent data, this opportunity is powerful as iDenfy’s identity verification solution combines document verification with advanced biometric verification measures to ensure that users are real and present in the process of onboarding. iDenfy’s multi-layered approach to identification assures real-time verification and effectively blocks the use of fake identities, phony photos, or physical disguises, making fraud significantly more difficult in real-time. Securing digital identities It’s worth mentioning that businesses in every industry are putting a higher emphasis than ever on strong identity verification to protect themselves. A recent report from Juniper Research on online fraud says that the global costs are likely to exceed $107 billion by 2029 year, with identity fraud being an important contributor, causing significant expense and distrust to operators and customers alike. With the growing tactics for committing fraud with sophisticated plans from bots to fake accounts, there has never been a greater demand for having a trustworthy identity verification solutions provider. Fighting survey fraud “Fraud is a massive issue in the market research industry. Ensuring that our clients receive accurate, high-quality data is paramount to our mission. Partnering with iDenfy allows us to offer a reliable solution to verify the authenticity of respondents and set us apart from competitors with a commitment to innovation and trust,” said Klaus Oberecker, the CEO of Reppublika Data Analytics & Technologies. Strategic partnership “We’re excited to partner with Reppublika, a company that is at the forefront of innovation in the market research industry. Our solution will help the business ensure that its clients deal with genuine survey respondents, maintaining the highest level of accuracy and trust, which is the key factor when working with data,” added Domantas Ciulde, the CEO of iDenfy.
Zivver, has reached a major milestone this year, preventing over Eight million data leaks and celebrating its tenth year in email security. Established in Amsterdam in 2015 by founders Dr. Rick Goud and Wouter Klinkhamer, the organisation now employs over 130 people across Europe and the United Kingdom. Trusted protection With a focus on various sectors Zivver’s email platform enables people to communicate securely Over the last decade, Zivver has evolved their product and entered new markets. The secure email platform serves over a million users across the Netherlands, United Kingdom, United States, Germany, France, and Belgium. With a focus on the healthcare, government, finance and legal sectors, Zivver’s email platform enables people to communicate securely with minimal disruption and minimises the risk of data leak. Recent enhancements to its product suite—featuring eSignature capabilities, file transfer and an inbound Email Threat Protection solution—further strengthen Zivver’s commitment to a comprehensive email security. These enable organisations to better protect sensitive information, uphold regulatory standards, and maintain the integrity of their communications. Securing communication Dr. Rick Goud, CIO and Co-Founder, of Zivver comments: "The last 10 years have been significant for both the Zivver team and the email security industry. A time of profound change, and despite data protection being taken more seriously, email remains the primary vector for cyberattacks.” “The rapid adoption of AI-generated cyberattacks has placed added pressure on organisations, reminding us that complacency is not an option. This is precisely why we expanded our focus beyond outbound email security.” “Looking ahead, Zivver is committed to delivering best-in-class security solutions that continually evolve to stay ahead of emerging threats, enabling organisations to communicate securely and confidently.” Securing the future Wouter Klinkhamer, CEO and Co-Founder added: “Our mission has always been clear: we want to simplify cybersecurity and make it more accessible. 10 years of Zivver is a fantastic achievement, and I’m proud to see it evolve from a small startup into the trusted organisation it is.” A decade of trust As Zivver celebrates a decade of innovation and success in secure communications, its growth demonstrates its commitment to its founding principle – achieving data security without compromising productivity. With a growing global presence and customer base, Zivver remains at the forefront of addressing the challenges of the digital communications in the decade ahead.
Detection Technology, a pioneer in X‑ray detector solutions, announces the launch of a first‑of‑its‑kind X‑Panel 2520z FOM flat panel detector designed to elevate dental imaging. This trend‑setting 25 cm x 20 cm detector is the first on the market to feature advanced IGZO‑TFT technology at this size, delivering a significantly larger field of view (FOV) and enhanced image quality compared to traditional a‑Si panels. X-Panel 2520z FOM features The X-Panel 2520z FOM sets a new benchmark in dental imaging with its advanced features: Enhanced field of view and resolution: An imaging area that is 95% larger with a resolution improvement of 30% when comparing to traditional a-Si panels, enabling the capture of full-resolution CBCT (Cone Beam Computed Tomography) scans with exceptional clarity. Accelerated imaging speed: With a frame rate of 25 fps (1x1) and 50 fps (2x2)—double that of conventional a-Si panels—this detector speeds up workflow without compromising image quality. Superior low-dose performance: The low-noise IGZO-TFT technology reduces electronic noise by approximately 50%, ensuring clearer images even at reduced radiation doses. Robust data handling: An integrated image buffer allows the entire scan to be stored in internal memory, minimising the risk of data loss during critical procedures. Compliance and sustainability: A lead-free version of the detector is available, ensuring full compliance with RoHS directives without exemptions. Diverse needs for dental imaging X-Panel 2520z FOM is created for dental CBCT imaging, offering wide imaging abilities The X-Panel 2520z FOM is designed primarily for dental CBCT imaging, offering expansive imaging capabilities. In addition to CBCT, it also provides versatility for panoramic imaging and has potential for cephalometric applications, meeting the diverse needs of dental imaging. The X‑Panel 2520z FOM is available in two variants, including a lead‑free version, ensuring full compliance with the RoHS directive without exemptions. These tailored options provide dental imaging OEMs (Original Equipment Manufacturers) with the flexibility to select the configuration that best meets their specific performance, cost, and regulatory requirements. Demand for imaging solutions "Building on the success of previous products like the X-Panel 1717z FDM, we are expanding our portfolio further to meet the growing market demand for complete and versatile imaging solutions." "The industry’s push for a larger FOV is met head-on with this new model,” says Tuomas Holma, Product Director at Detection Technology. Future of dental imaging Holma added: "Our commitment to local manufacturing and comprehensive service—across Finland and China, and a growing presence in India—ensures shorter response and delivery times, and cost-effective local product solutions, all while maintaining high standards of quality. Our strong brand image, built on high performance, reliability, and user-friendliness, makes us the preferred partner for dental imaging OEMs." Evaluation units will be available in Q2 2025. Detection Technology will showcase the X-Panel 2520z FOM and its key features at the IDS exhibition in Cologne, Germany, from March 25–29, 2025. Visit the team at stand T049 to experience the future of dental imaging firsthand.
Corporate Security Advisors (CSA), the premiere management consulting firm specialising in corporate security, announced that it has been selected to join the prestigious American Hospital Association (AHA) Preferred Cybersecurity and Risk Provider Program as the first Preferred Physical Security Advisory Services Provider. CSA will play a critical role in helping hospitals and healthcare systems nationwide enhance their physical security strategies to protect patients, staff, and facilities. Escalating physical threats “Corporate Security Advisors has been selected by the AHA as a premiere solution provider for their physical security advisory services and their security executive recruiting, coaching and organisational design service. We can confidently recommend Corporate Security Advisors as an outstanding professional resource for our nation’s hospitals and health systems in their efforts to protect their patients and staff from harm,” said John Riggi, National Advisor for Cybersecurity and Risk at the AHA. “In an era marked by escalating physical threats, CSA’s strategic, business-aligned approach to security empowers healthcare organisations to mitigate risks in a patient-friendly manner while delivering bottom-line operational success,” said Jeremy Baumann, CEO of Corporate Security Advisors. Elevating security standards in healthcare With decades of experience advising some of the largest and most reputable healthcare systems in the country, CSA is uniquely positioned to deliver tailored solutions that address the complex challenges faced by healthcare providers. These services include: Comprehensive physical security program assessments Development of strategic roadmaps and business plans aligned with business objectives Organisational design and executive recruiting for high-performing security pioneers and teams Evolving security risks “Hospitals are places where patients and staff must be focused on care and healing,” said CSA’s Jeremy Baumann, adding, “A high performing security organization, strategically-aligned and mission-focused, contributes significantly to this environment of healing." "Through this designation from the AHA, we can equip AHA member hospitals with actionable strategies and plans to safeguard their patients and staff against evolving security risks. Our approach ensures security measures support broader organisational goals and enable uninterrupted delivery of world-class care.” A partnership for the future of healthcare security CSA shares AHA’s vision and commitment for fostering safer, more resilient healthcare environments by addressing pressing security risk challenges such as workplace violence, active shooter scenarios, and the security complexities of densely populated urban areas. “The safety of our healthcare workforce and the patients they serve is a cornerstone of effective care delivery,” AHA’s John Riggi added. “By leveraging CSA’s expertise, the nation’s hospitals can proactively enhance their security posture, ensuring they remain sanctuaries for healing and recovery.”
Wavelynx Technologies, a pioneer in secure and versatile reader and credential solutions, has expanded its global reach into the United Kingdom and Ireland to support the increasing demand for modern security solutions. This strategic move comes as the company scales its operations to ensure that all customers have access to interoperable solutions that align with the growing need for advanced security across sectors such as commercial real estate, hospitality, education, and healthcare. Evolving security landscape "As global demand for flexible and interoperable security solutions accelerates, expanding into the UK and Ireland is a strategic next step for Wavelynx," said Rob Lydic, President of Wavelynx Technologies. "This expansion strengthens our international presence and positions us to better serve a growing global customer base. As businesses prioritise secure, scalable access control, we are committed to delivering innovative solutions that provide flexibility, choice, and control—empowering both end users and system integrators to stay ahead in an evolving security landscape." Strengthening security measures The global access control market is projected to grow at a compound annual growth rate (CAGR) of 8% The global access control market is projected to grow at a compound annual growth rate (CAGR) of 8% through 2032, as businesses prioritise safety and security. Rising demand for advanced, interoperable systems—particularly those supporting mobile credentials and keyless technology—is further fueling this growth. In the UK and Ireland, this need for scalable access control technologies reflects a broader shift towards strengthening security measures and improving operational efficiency. Driving efficiency and adaptability Wavelynx's expansion into the UK and Ireland will enable businesses to modernise their technology stack at their own pace, setting new standards in security innovation. To spearhead these efforts, the company has appointed Joe Page as Manager of Business Development for the region. A seasoned pioneer in the security and technology sector, Page will drive expansion initiatives, leveraging Wavelynx's robust portfolio to meet the evolving needs of the market. "It's an exciting time to join Wavelynx as we expand our global footprint," said Page. "The UK and Ireland are key markets for us, and I'm eager to help businesses across the region modernise their access control systems with innovative, secure solutions that drive efficiency and adaptability."
Xtract One Technologies announced its Xtract One Gateway (“Gateway”) has been selected to protect key hospital locations in Manitoba, including the province’s Health Sciences Centre and Crisis Response Centre locations operated by Shared Health. The system will redefine the security experience by balancing powerful threat detection with the seamless flow for individuals, enhancing safety standards, and optimising operational efficiency. Securing health facilities "Healthcare environments today face two security challenges: providing top-tier security while ensuring that both patients and caregivers feel safe and comfortable," said Peter Evans, CEO of Xtract One. “This is a trend we’re seeing across the healthcare sector, where providers are actively looking for solutions to these growing challenges, and we welcome the opportunity to play a role in securing health facility environments.” Screening solutions portfolio Xtract One’s screening solutions portfolio is designed to scan individuals and their belongings. These solutions allow seamless passage through checkpoints and reduce the need for separate bag searches, thereby dramatically improving screening times. Gateway unobtrusively scans individuals, their pockets, tags, and backpacks for potential mass casualty weapons while distinguishing harmless personal items like laptops, tablets, three-ring binders, notebooks, eyeglass cases, keys, and phones. This streamlines access into and out of facilities without disrupting the flow of movement.


Expert commentary
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realise, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionising the overnight security business. Minimising criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilises a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimise the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is remote guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilises a combination of methods to effectively analyse potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyse the situation in real-time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command centre, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customised remote guarding When properly deployed, remote guarding systems are also customised to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional security shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A bounty of benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilise targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyse incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilise this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilises a decentralised ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralised, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimise threats or attacks to organisations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorised entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorised entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organisation. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organisation to undergo authentication, authorisation, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilises the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organisations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organisations in proper data control, handling, and security. These policies guide organisations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Daniel May of Consort reviews the integration of access control systems in healthcare settings, outlining the benefits and key considerations decision-makers must make throughout product specifications. From patient safety and traversal to the protection of sensitive data and pharmaceuticals, healthcare environments are faced with several operational challenges. And where security remains at the forefront of decision-making, modern access control systems may often hold the answers. Physical security systems Hospitals in particular have developed into multi-faceted spaces that house hundreds to thousands of patients, staff and visitors at any one time. In England for example, research has found in the three months leading to June 2023, an average of 44,626 people visited major hospital A&E departments each day, with over 16 million attendances typically recorded over the course of a year-not to mention an additional nine million logged at other minor units. For any building, this level of sustained footfall can request severe security difficulties For any building, this level of sustained footfall can invite severe security tests. With that, the need to deploy effective physical security systems in healthcare is clear. And so, as access control continues to become more readily adopted and new products enter the market, decision-makers are reminded to consider the requirements of their building, ensuring they select the solutions most suited to their settings and budget. Security controlled Patient safety will always remain the top priority in healthcare settings, and where matters of health and social care come into question, a diverse set of professional regulatory bodies are tasked with setting and maintaining high standards. When it comes to healthcare premises specifically, patient security and perimeter security often come hand in hand and are amongst the most pressing of challenges that decision-makers must face. To help address operational planning and potential design concerns in the NHS, the Health Building Note (HBN), provides general design guidance for healthcare buildings under HBN 00-01-citing the use of access control measures as a way of maintaining security and protecting the safety of patients, staff and visitors. Use of access control Hospital buildings control varied levels of access for a number of security purposes Hospital buildings, for example, must control varied levels of access for a number of operational and security purposes. Routine scenarios exist where vulnerable patients are under monitoring and thus refrained from exiting the premises for their own safety, while at the same time, permitted staff must be able to reach their patients and medicines when required. For this, the use of access control is key. Equally, access credentials can also help management teams keep track of those who may be entering or exiting rooms with equipment and pharmaceutical supplies, deterring any unwanted visitors and opportunists in the process. Incorporation of access control systems On a similar note, regulations have set a minimum standard for how personal data should be stored and managed in healthcare environments, giving decision-makers an added responsibility to regulate staff-controlled areas with patient medical records. While instances of personal data breaches are rare, healthcare facilities and professionals are at legal risk should confidential data be found misused or missing. As such, the incorporation of access control systems has become essential in keeping data storage areas secure, with intuitive online systems capable of permitting access to staff with the correct credentials while simultaneously tracking who has requested clearance at digital entry points. HBN guidance Healthcare experts are better fitted to control the sheer volume of people entering and exiting To function effectively, healthcare facilities must always be perceived as safe places by the people who reside within them, and as HBN guidance implies, a unified physical security system can help address key safety and security concerns while enhancing patient and staff experience. Opportunely, access control systems are more accessible and adaptable than ever and combine several technologies such as mechanical locks and automatic doors with electronic access credentials in the form of smartphone apps, badge readers and biometric scanners. By integrating these systems into the building’s existing infrastructure, healthcare professionals are better equipped to control the sheer volume of people entering and exiting the premises without impairing the general flow of movement and coordination around the facility. Better by design Despite the clear benefits offered to healthcare facilities, there are a number of considerations to be mindful of when choosing an access control solution. Poorly implemented systems can have an adverse effect on security and functionality - quickly costing healthcare organisations time and budget to rectify and replace the inadequate products that don’t meet the building’s requirements. For that reason, decision-makers and design teams are reminded that there is no single solution that fits all healthcare buildings. As such, it’s crucial for decision-makers to understand the systems that are being put in place throughout each of the touchpoints in their facility. Clear collaboration is required during periods of specification, where together, teams can ensure the selected product works on all angles, from meeting fire safety and sustainability standards to aesthetics and scalability. Modern access control products Scalability is a key area that decision-makers must review when selecting access control systemsFrequently overlooked, scalability is a key area that decision-makers must review when selecting access control systems. Such is their diverse nature; healthcare facilities can often change and develop as years go by, and by selecting a system that facilitates growth, such as a cloud-based solution-security and efficiency is long-established. While modern access control products are known for seamless integration, there are some systems that may restrict the ability to use different vendors throughout the remainder of the building’s infrastructure. This, in effect, causes a monopolisation of products throughout the estate, which can have an adverse effect on growth by increasing costs and reducing the levels of service associated with the security system already in place. Improve security and safety A scalable and reliable access control system will continue to improve security and safety by adapting to a building’s new requirements-and all while having minimal impact on its operational network. And so, while technology will no doubt continue to influence and transform the access control market, healthcare facilities and their professionals must continue to remain educated on their own systems, ensuring they have the best options in place to keep their patients, staff and visitors safe and secure for years to come.
Security beat
Companies at GSX 2023 emphasised new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasises ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the mid-market to the cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for the pure cloud, but there are benefits to be realised from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realise the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘soft’ features for integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organisation more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organisation more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centres around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasising performance, protection (cybersecurity), and price, their data centres are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring centre where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
PKOC stands for Public Key Open Credential. It is a new standard that will meet a 30-year industry challenge and strip away much of the complexity and cost involved in protecting and administering credentials for access control. It could also accelerate the transition from cards to mobile access control. PKOC is a standards-based mobile credential that is essentially free, vendor-agnostic, and interoperable across multiple devices and systems. It is a highly secure access credential that can live on a mobile phone, in a plastic access card, or in any device capable of generating a public-private key pair. Access control systems PKOC is the newest standard of the Physical Security Interoperability Alliance (PSIA), a tax-exempt organisation created to define, recommend, and promote standards for IP-enabled security devices and systems. PSIA introduced the Physical Logical Access Interoperability (PLAI) specification in 2013 to normalise identity data across disparate physical access control systems. The PKOC specification was introduced in 2021. We’re convinced this is the future A challenge for PSIA in promoting the PKOC mobile credential is to explain it quickly and in layman’s terms “We see the benefit of implementing the PKOC technology and doing it well,” says Sam Siegel, Senior Field Applications Engineer for ELATEC, a manufacturer of credential-agnostic readers/writers. “We wanted to get involved and join the discussion.” ELATEC has been participating in PSIA for more than a year. “This is a better way to do things,” says Siegel. “The PSIA, myself included, are convinced this is the future. The challenge is to get enough people to understand that it is a seismic shift away from what has been in place for so long.” A challenge for PSIA in promoting the PKOC mobile credential is to explain it quickly and in layman’s terms. The explanation spans the concept of public key infrastructure (PKI) and the difference between symmetrical and asymmetrical digital keys. Protecting symmetrical keys A symmetrical key system, which has been used historically in the access control market, involves the use of a single proprietary digital key to both encrypt and decrypt information. This means that digital public keys must be incorporated into each access control reader in the form of a module or a license, which the reader uses to read any compatible cards. Protecting symmetrical keys has been an expensive technology challenge the access control world The need to share these digital keys (in effect, the ability to read every compatible card) securely among access control manufacturers, integrators and end users involves extra administration and costs to ensure the security of the system. Protecting symmetrical keys has been an expensive technology challenge the access control world has borne for decades. The use of proprietary keys also promotes dependence on a single manufacturer or vendor to expand the ecosystem. The use of asymmetrical keys takes away these challenges. Advantages of using asymmetrical key pairs PKOC embraces the principle of PKI (public key infrastructure), a two-key asymmetrical system used to ensure confidentiality and encryption. In effect, there are two digital "keys," one public and one private, that are used to encrypt and decrypt information, in this case, a credential for an access control system. The secure credential standard is generated independently of a third-party credential issuer. It is generated within the device. In the access control scenario, the smartphone generates a key pair in the secure element of the phone, including a private key, which is stored on the smartphone, and a public key, which serves as the user’s ID number in the access control system. Sharing the public key is not a security risk because it is worthless without the private key that is locked away on the smartphone. PKOC-enabled smartphone The smartphone must contain the private key in order to interface with the access control system When a PKOC-enabled smartphone approaches a PKOC-enabled reader, the reader sends a one-time random number (a ‘nonce’) to the smartphone, which then encrypts it using the private key, and sends it along with the public key back to the reader. The reader uses the public key to decrypt the random number, which confirms the authorised access associated with the smartphone. The signals are sent via Bluetooth Low Energy (BLE). Importantly, the private key never leaves the smartphone and is never shared with any other elements of the access control system. Therefore, there are no administrative or technical costs associated with protecting it. The smartphone must contain the private key in order to interface with the access control system using the public key. Mobile credentialing system For ELATEC, embracing PKOC provides a new way to highlight the company’s value proposition and promote it to a new group of companies; i.e., those who adopt the PKOC approach to mobile credentialing. The ‘universal’ configuration of the ELATEC reader hardware is credential-agnostic “PKOC serves as a great way to show off our value and what we do best,” says Siegel. ELATEC provides credential readers/writers that operate in a variety of card and reader environments, incorporating an integrated BLE module to support mobile ID and authentication solutions, including PKOC. Using applicable firmware, the ‘universal’ configuration of the ELATEC reader hardware is credential-agnostic and so compatible with any RFID card or mobile credentialing system, all in a small form factor (around 1 1/2 inches square). How readers and smartphones interact The PKOC standard addresses the variables of how the reader and the smartphone share information. Currently, the PKOC standard addresses communication via BLE, but the principle is the same for systems using near-field communication (NFC), ultra-wideband (UWB), or any future protocols. PKOC also defines how device manufacturers can enable devices (readers, locks, control panels, biometric devices, etc.) to securely consume the credential for authentication and access. PKOC can be used with smart cards as well as with smartphones. In the case of a smart card, the public and private keys are contained on the smart card, which communicates via NFC with the reader. The encryption/decryption scenario is exactly the same. PKOC enables users to ‘bring your own credential’ (BYOC). Public key number ELATEC is proud to have played an instrumental role with the PSIA in the implementation of PKOC" BLE offers a broader read range than NFC; the read range can be managed using software and/or by signalling intent or two-factor authentication. Because private keys remain secure inside a smartphone, they do not have to be incorporated into a digital wallet for security purposes, although they could be incorporated for matters of convenience. To simplify administration, the public key number can be used as a badge number. If badge numbers have already been assigned, a column could be added to the database to associate badge numbers with public key numbers. “ELATEC is proud to have played an instrumental role with the PSIA in the implementation of PKOC,” said Paul Massey, CEO of ELATEC, Inc. “End-users should not be limited in their solution mix to one or two vendors due to their proprietary technology. PKOC now provides the ideal combination of security, convenience, interoperability, and cost for industry participants, by industry participants.” ‘Experience PSIA’ will promote PKOC at ISC West ISC West participants include PSIM manufacturer Advancis Software and Services The flexibility of PKOC will be on display at ISC West 2023, where ‘Experience PSIA’ will register attendees and provide them with a PKOC credential that can be used with a variety of readers throughout the show. Also showcasing the PLAI standard, PSIA’s presence at ISC West will include ELATEC along with several other vendors/manufacturers. A special PSIA event will be held from 5:30 to 7:30 p.m. on March 29 at the Venetian Ball Room B&C in Las Vegas. ISC West participants include PSIM manufacturer Advancis Software and Services, which acquired Cruatech software in 2012; and Idemia, specialising in identity-related security services including facial recognition and other biometrics. Integrated security systems Also involved are Johnson Controls (JCI), an integrated security systems provider that offers a range of security products and services; and Siemens, which offers its own range of security solutions and systems. Other participants include Last Lock, which has a unique spin on internet-enabled locks; while SAFR from Real Networks offers accurate, fast, unbiased face recognition and additional computer vision features, and Sentry Enterprises provides the SentryCard biometric platform for a privacy-centric, proof-of-identity solution. Finally, rfIDEAS manufactures credential readers.
Milestone Systems wants to double its revenue in the next five years while also setting a new standard of how technology companies behave, spotlighting more responsible use of technology. In short, the open platform video management system (VMS) company seeks to revolutionise the industry, deploying data-driven video software in security and beyond. Milestone is also shifting the approach from tech-centric to emphasising business outcomes; that is, focusing on solving problems that keep their customers up at night. Integration partner program “Technology companies have a bad habit of falling in love with their own products,” says Thomas Jensen, Milestone CEO. “But if we cannot convey to customers what the products will do for them, then shame on us. We want to focus on business outcomes as the way we address our customers, drive business, and add value to companies. We want to focus on outcomes rather than the functions products perform.” We want to focus on business outcomes as the way we address our customers" At the MIPS 2022 Partner Summit in Minneapolis, Milestone outlined for their integrator and technology ‘partners’ the path to achieving these lofty goals. The vision includes revamping the integration partner program to eliminate two-thirds of their dealer count, with the remaining third more focused on Milestone and equipped with new marketing tools to succeed at even higher levels. Market development personnel MIPS (Milestone Integration Platform Symposium) is a combination education seminar, pep rally and mini-trade show. The yearly event continued virtually during the pandemic and is back in 2022 as a fully in-person experience — first in Dubai and then in Minneapolis for the Americas market. Milestone is also dramatically increasing its head count as an investment in the future, emphasising a ‘people-first’ mindset that sets the company apart, says Jensen. In the Americas market, Milestone has increased the size of the organisation by 75% in the last year. They have increased sales personnel 100% during that time, upped pre-sale technical personnel by 150%, and increased market development personnel by 200%. Cloud-based setups The future of data-driven video technology will include a mixture of on-premise systems, cloud-based setups, and a combination of the two (hybrid) Milestone intends to spend more money on marketing to reflect the evolving ‘buying journey’ of business-to-business customers, who often do more online research before reaching out to vendors. The new Milestone vision also requires a heightened focus on vertical markets, including applications beyond traditional security use cases. It also embraces cloud systems for small- to medium-sized businesses. The future of data-driven video technology will include a mixture of on-premise systems, cloud-based setups, and a combination of the two (hybrid). To expand their cloud offerings, Milestone announced the introduction of Kite, a Milestone-branded version of the cloud system developed by Arcules, a Canon sister company built on the Google cloud. The ‘pure cloud’ system, targeting small- to medium-sized businesses, will be offered in addition to a previously announced version of XProtect hosted by AWS (Amazon Web Services). The new Milestone vision also requires a heightened focus on vertical markets Safe cities applications Examples of applications ‘beyond security’ include use of video technology in safe cities applications to learn traffic patterns, adjust traffic flow, etc. In 2023, Milestone will launch XProtect Hospital Assist, targeting the healthcare vertical with applications beyond hospital security. For example, the system will address the shortage of nurses using video systems that can help to monitor patients remotely and detect falls. Blurring technology, applied per camera and in real time from a smart camera interface, will be used with video to protect patient privacy. Industry-based solutions “Each industry has different use cases, especially beyond security,” says Anders Bo Rasmussen, Director Product Direction at Milestone. “The demand is also increasing, which makes it difficult for a generic product to succeed. We are investing in finding more industry-specific use cases and transitioning to industry-based solutions. We must understand the language and the need to create intimacy that will eventually give us the business. We can be more competitive, more focused, and stand out more.” Another new vertical market product will address the hospitality industry, including gaming Another new vertical market product will address the hospitality industry, including gaming. Among other capabilities, the system can use video and facial recognition to recognise compulsive gamblers. Supporting casinos to meet legal requirements, the system will create value beyond video and beyond safety and security. Promoting human rights For one customer, a Milestone system ties together connected video and sensors on a cruise ship to respond to silent alarms without alerting guests that there is a problem. Another example involves using video in remote therapy sessions with children on the autism spectrum. Expanding in markets beyond security depends on Milestone being able to map the right stakeholders and broaden the appeal to other departments in a company. Security will continue to be the ‘gateway’ to additional business, at least in the near term. Security will continue to be the ‘gateway’ to additional business, at least in the near term Related to the responsible use of technology, Milestone subscribes to the United Nations Guiding Principles on Business and Human Rights, embracing emerging awareness of the responsibilities of business to promote human rights around the world. In practice, the commitment guides Milestone to avoid unconscious bias in products and recruitment and to perform due diligence when approving projects to ensure they do not impact human rights. Acceptable standards of surveillance Milestone has also taken a deliberate stand not to do business with companies that violate human rights. Another concern is responsible use of data. “Here is a warning for our industry: The Wild West is over,” says Jensen. “It’s our responsibility to use data in a responsible way. Now is the time to act to protect our current and future generations.” Responsible technology also extends to uses of artificial intelligence (AI), ensuring that a human directs system intent and complying with acceptable standards of surveillance throughout the world.
Case studies
Smart Hospital Bacău, a major medical institution in Romania, has taken a huge step forward in improving patient care and operational efficiency. The hospital has introduced auxiliary care and fall detection radars, along with thermal presence detectors from Hikvision. It’s a great example of how smart devices can transform healthcare, leading to better outcomes for both patients and medical staff. Enhancing palliative care Smart Hospital Bacău offers palliative care as an essential part of its services Smart Hospital Bacău offers palliative care as an essential part of its services. Because of their fragile health conditions, palliative care patients often need round-the-clock monitoring. The hospital recognised this need and was eager to enhance its capabilities in this area. Traditional nurse call systems have limitations, as they depend on patients being conscious and able to press a button, which is not always possible for severely ill or less mobile patients. However, the hospital was aware of these constraints and was determined to find better solutions. Real-time monitoring tools Previously, the hospital relied on manual patient checks, paper records, and verbal shift-to-shift communication. While these methods have been part of the healthcare routine, they put a heavy workload on staff. Without real-time monitoring tools, the hospital's care approach was more reactive. But the hospital saw this as an opportunity for growth and was committed to safeguarding patients and staff from preventable incidents. Hikvision's comprehensive healthcare solution To address these challenges, Smart Hospital Bacău partnered with Next M, a major technology solution provider, to implement a smart healthcare solution using Hikvision products. The solution included auxiliary care radars, fall detection radars, thermal presence detectors, touchscreens, and a centralised LCD display, all integrated into the hospital’s nurse call platform. In the palliative care rooms, each of the 30 beds were equipped with Auxiliary Care Radars (DS-TDSB00-EKH/POE/2m) and Bedside Touchscreens (DS-KHH9530-H(O-STD)/M). The radars can monitor heart rate and respiration without the need for patients to wear any devices. Info World Mobile module These radars also detect bed presence, sleep patterns, and abnormal movements, sending real-time alerts These radars also detect bed presence, sleep patterns, and abnormal movements, sending real-time alerts to nurses when there are issues. The touchscreens had the Info World (IW) Mobile module deployed by the healthcare software expert Info World. They ensured full software integration with hospital databases, interoperability with the hospital info and pharmacy systems. Through secure Android integration, the touchscreens serve as point-of-care digital assistants that enable medical staff to access patient records at the bedside. Fall Detection Radars In high-risk areas like bathrooms, Fall Detection Radars (DS-TDSB00-EKT/POE/4m) were deployed. They can spot sudden posture changes or long stays, enabling staff to respond quickly to emergencies, while protecting patient privacy. The hospital also installed 15 Thermal Presence Detectors (HM-TD1018-1/QR). These devices combine thermal imaging and radar technology to provide non-intrusive monitoring of patient movement, including out-of-bed detection, exit alerts, and audio alarms for events like calling for help. Finally, a 55-inch LCD display (DS-2055HE-G) was placed in the nurse room. It serves as a centralised hub, providing real-time alerts and monitoring details through the HikCentral platform. Multi-layered approach The integration of these technologies into a unified system enabled faster and more informed responses This multi-layered approach ensures comprehensive coverage, with each device tailored to specific monitoring needs. The integration of these technologies into a unified system enabled faster and more informed responses to patient incidents, significantly enhancing both safety and efficiency. Improving medical workflows The Hikvision smart healthcare solution has brought great benefits to the staff and patients at Smart Hospital Bacău. The system has automated routine checks, greatly improving medical workflows. Nurses no longer need to do frequent manual rounds. Instead, they now receive real-time alerts for abnormal events and can focus on patients who really need help. This reduces human error, improves time management, and eases staff burnout. The centralised display in the nurse room gives instant access to monitoring data, making coordination easier and enabling better decision-making through trend analysis. Patient safety and well-being Hospital Manager, Ciprian Cojocaru, praised the solution, stating: “Before this system, we constantly did rounds to check on patients. Now we know exactly when and where to step in. It has greatly improved our confidence and response times.” Patient safety and well-being have also been significant improved. The system continuously and non-intrusively monitors patients. It can immediately detect emergencies like falls or breathing problems, even for patients who are unable to call for help. Faster responses reduce the risk of incidents getting worse. Privacy-friendly technology The privacy-friendly technology, which operates without video, makes patients more comfortable. Additionally, information from the devices helps create more personalised care plans. Medical teams can spot early signs of health decline and proactively adjust treatments. Beyond these immediate benefits, the implementation of the Hikvision solution has also enhanced the hospital's reputation as a modern, forward-thinking institution. Its adoption of smart healthcare sets a new standard for palliative care, earning the trust of both patients and medical professionals.
A.C. Camargo Cancer Centre, a pioneering oncology treatment centre in São Paulo, Brazil, recognised for its history of innovation, announces that its partnership with Axis Communications has produced savings of more than $2 million over its first two years, all of which will be reinvested in patient care. A.C. Camargo has deployed more than 2,000 state-of-the-art video surveillance cameras throughout the Centre’s corridors, complex care units, and parking lots, embracing a more holistic approach to security that emphasises patient and employee safety along with improved quality of service. Hospital’s security infrastructure Founded in 1953, A.C. Camargo treats an estimated 100,000 patients annually and is one of the world’s largest healthcare institutions and a pioneering provider of cancer treatment and research. Prior to partnering with Axis, financial losses due to theft were a growing concern for A.C. Camargo The Centre is not just a hospital, but a comprehensive care platform that includes prevention, investigation, staging, treatment, palliative care, and rehabilitation services for all types of cancer. Prior to partnering with Axis, financial losses due to theft were a growing concern for A.C. Camargo, and hospital pioneers sought to transform the hospital’s security infrastructure in a way that would both enhance its security posture and streamline patient care and services. Advanced new video surveillance devices “Nearly 15,000 people pass through our entrances each day, and caring for those patients extends far beyond operating or patient rooms,” said William de Souza, Corporate Manager at A.C. Camargo Cancer Centre. “By deploying advanced new video surveillance devices, we are enabling our security teams to maintain round-the-clock vigilance and our medical personnel to provide the highest quality of care to our patients." "With cameras monitoring all areas, including cafeterias and parking lots, we are always looking for potential warning signs—even after patients have been discharged. If anything seems amiss, we can alert our team that additional medical care may be needed.” Key national and international certifications The Axis devices are equipped with video analytics that allow the Centre to go beyond asset protection. These analytics are deployed with a high degree of sensitivity to ensure high-quality care for patients, their families, and the nearly 6,000 staff members on-site daily, while also protecting their privacy. Axis cameras have enabled the A.C. Camargo Centre to improve operations and meet key national and international certifications through: Increased Operational Efficiency: The system enhances operational efficiency by proactively detecting critical issues such as power outages, water leaks, and equipment malfunctions – including refrigerators used for medication storage. This early detection helps prevent medication loss and limit downtime. Additionally, the system can identify nitrogen leaks and immediately trigger luminous alerts, enabling staff to respond quickly and prevent potentially hazardous situations from escalating. Optimised Parking Management: With more than 300,000 vehicles passing through the Centre’s parking facilities each year, traffic management is critical. The new system helps streamline the process by automatically identifying licence plates belonging to authorised vehicles. Enhanced Patient Care: By providing continuous monitoring in critical areas, such as surgical centres, and delicate procedure rooms, like cellular medicine and pathology, the system enhances patient safety while maintaining strict compliance with privacy regulations. Emergency Management Solutions: Cameras throughout the facility are equipped with analytics that detect falls and suspicious behaviour and can even assist in identifying and preventing situations where individuals in distress might harm themselves. Integrating video surveillance cameras Both A.C. Camargo and Axis Communications remain committed to further implementing solutions “The implementation of Axis solutions at A.C. Camargo Cancer Centre underscores what is possible when innovation is paired with a deep commitment to care,” said Carlos Machado, End Customer, Key Account Manager, Brazil at Axis Communications. “By integrating video surveillance cameras enhanced with analytics, the Centre has made safety a central pillar of its operations, allowing staff to fully focus on what matters most: the health and comfort of their patients. By doing so, hospital leadership has set a compelling example for other institutions facing similar challenges.” Improvement in patient outcomes After initially implementing 300 cameras, A.C. Camargo quickly noticed a difference. The Centre moved to further scale the system, adding hundreds of additional cameras to achieve greater coverage throughout its facilities. Now, there are a total of 2,100 cameras throughout the seven buildings that make up the Centre. Looking to the future, both A.C. Camargo and Axis Communications remain committed to further implementing solutions that support continuous improvement in patient outcomes and operational effectiveness.
Comelit-PAC has successfully upgraded the access control infrastructure at Blackpool Victoria Hospital, ensuring a seamless and secure environment for staff, patients, and visitors. Blackpool Victoria Hospital is one of the largest and busiest hospitals in the Northwest, providing essential healthcare services to thousands of patients each year. As a pioneering medical facility, ensuring a secure and efficient environment is a top priority. Integrated PAC Access Central Security technology works programme integrated PAC Access Central with multiple PC workstations Designed to provide a robust and scalable security solution, the security technology works programme integrated PAC Access Central with multiple PC workstations for comprehensive global administration across the hospital’s network To safeguard critical areas within the hospital, Comelit-PAC’s advanced 500 series controllers were utilised. This includes the 511, 512 model door controllers linked into the existing 500 Access & Alarm servers on site, offering a mix of ethernet and RS485 connectivity to enhance system flexibility and efficiency. Security and administrative control Martyn McKechnie, Head of Digital Identity at Blackpool Victoria Hospital, commented: "As a busy hospital with multiple departments and critical areas, we required an access control system that could integrate seamlessly while offering high levels of security and administrative control." Martyn McKechnie adds, "PAC Access Central provides the scalability and reliability we need to manage hospital-wide access efficiently. The ability to oversee all access points from multiple PC workstations ensures our Digital Identity and Security teams can respond quickly to any situation." Future-proof access control system Blackpool Victoria Hospital benefits from a resilient and future-proof access control system A key element of the installation is its server-based architecture, providing enhanced security measures and fail-safe redundancy. This ensures Blackpool Victoria Hospital benefits from a resilient and future-proof access control system, capable of meeting the bespoke demands of the healthcare environment. Advanced security infrastructure Jason Sullivan, PAC/GDX Strategic Development Manager at Comelit-PAC, said: "We worked closely with Blackpool Victoria Hospital right from the initial specification stage to deliver a solution to balance security with ease of management." Jason Sullivan adds, "PAC Access Central presents a future-proof system that allows the hospital to maintain strict access control, while adapting to evolving needs. By adopting this advanced security infrastructure, Blackpool Victoria Hospital continues its commitment to maintaining a safe and secure environment, leveraging Comelit-PAC’s expertise in access control technology."
Hospitals face complex security and operational challenges, but BriefCam’s AI-driven Video Analytics Platform is transforming how organisations like Massachusetts General Hospital (MGH) address them with impressive results: Efficiency Boost: Review one hour of video in just one minute, allowing staff to focus on critical tasks. Rapid Incident Resolution: Quickly locate missing patients and identify individuals involved in incidents using streamlined video searches. Proactive Planning: Accurately quantify visitor traffic to the hospital's museum for better operational resource management. “We can take eight hours of video, and BriefCam creates the ability for somebody to go through it in less than an hour,” said Bonnie Michelman’s, CPP, Director of Police, Security and Outside Services at MGH Hi Business Associate.
In response to the increased demand for oxygen supplies following the 2020 pandemic and subsequent rise in respiratory-related conditions, Jacksons Fencing completed a key project in 2024 to safeguard vital oxygen storage facilities at a pioneering UK hospital. Addressing the demand The pandemic highlighted the critical role of oxygen in treating patients, causing a surge in its use across hospitals. Some facilities even declared major incidents due to oxygen shortages, prompting a significant government investment of over £15 million to upgrade oxygen supplies and prevent future disruptions. As part of these improvements, many larger hospitals have started to feature on-site liquid oxygen storage facilities, where vast industrial tankers convert liquid oxygen to gas as needed. Securing essential resources Jacksons Fencing provided and installed a comprehensive security solution for a new oxygen storage compound Given the stringent safety requirements associated with liquid oxygen due to its extremely low temperatures, precise pressure needs, and related fire and explosion risks securing and managing these supplies is paramount. To address these needs, Jacksons Fencing provided and installed a comprehensive security solution for a new oxygen storage compound. Robust fencing solutions with invisible screen The installation includes 38 metres of Securi-Mesh® fencing, standing at a robust height of 2.4 metres. This fencing is mounted on concrete hardstanding and is complemented by two cantilever sliding gates and a single-leaf pedestrian gate with a push pad exit and key entry. Securi-Mesh fencing features a tightly woven mesh pattern designed to deter climbing attempts, and its small apertures significantly improve resistance to cutting. Additionally, the mesh provides an ‘invisible screen’ effect that allows for effective surveillance without obstructing views, facilitating quick issue identification. Space efficiency and secure gating Unlike traditional swing gates, these gates slide parallel to the fence line, requiring minimal space The cantilever sliding gates installed are particularly well-suited for the restricted space in front of the facility. Unlike traditional swing gates, these gates slide parallel to the fence line, requiring minimal space both in front of and behind the fence. This design not only maximises space efficiency but also enhances security with quick operational cycles, allowing for faster vehicle and goods transit, reducing the time the gates remain open, and minimising security risks. 25-year guarantee with reduced maintenance Furthermore, the absence of ground tracks for the cantilever gates reduces maintenance needs by preventing issues related to debris or track damage, causing fewer repairs, and reduced downtime. In addition to these features, the fencing and gates are backed by a 25-year guarantee, ensuring long-term durability and minimal maintenance. Barbican® vertical bar fan panel The green polyester powder coating chosen for the fencing provides extra corrosion resistance The green polyester powder coating chosen for the fencing provides extra corrosion resistance and contributes to lower long-term costs for the hospital. Sections of the fencing, installed at varying heights, are further secured with a Barbican® vertical bar fan panel, which offers both a physical barrier to intrusion and a visual deterrent. Oxygen storage facility security Peter Jackson, Managing Director, of Jacksons Fencing comments on the success of the project, "Contributing to this vital project, enhancing the security of oxygen storage facilities at a UK hospital, is a significant achievement." "The pandemic highlighted the crucial role of oxygen, we must safeguard these resources effectively." Securi-Mesh® fencing and cantilever sliding gates "The integration of our Securi-Mesh® fencing and cantilever sliding gates reflects our commitment to providing both superior protection and operational efficiency." "By addressing the specific security needs of these vital resources, we help ensure that hospitals can focus on delivering high-quality patient care without disruption.”
The Marin Hospital of Hendaye in the French Basque Country faced common challenges posed by mechanical access control. Challenges faced Relying on mechanical lock-and-key technology made it difficult or impossible to know who had been accessing sensitive areas like treatment rooms and medicine stores. Another source of insecurity was the keys and passes issued to employees and contractors. These often remain in circulation beyond their approved use period, if former employees and service providers fail to return them. Need to upgrade access control To provide proper security for staff and patients, the hospital needed to upgrade its access control system To provide proper security for staff and patients, the hospital needed to upgrade its access control system. Meeting the demands of a large and complex site requires a flexible solution that can secure interior and exterior hospital doors, as well as multiple other types of openings. Also critical for The Marin Hospital of Hendaye is the ability to trace staff and external contractor movements into and between sensitive areas. An electronic access system with inbuilt audit trail capability was essential. Hospital access is traceable and tailored to user profiles The hospital chose an eCLIQ system based on programmable electronic keys and wireless cylinders. Since 2016, their security team has gradually rolled out eCLIQ electronic access control to all care and logistics buildings, including drug stores, labs, and other sensitive or confidential areas. The wireless eCLIQ solution offers easy installation without the expense or disruption of laying dedicated cabling. Quick and wireless installation “The choice of this solution is based on reliability and simplicity of implementation for a site that covers 11 hectares,” explains Yves Bourdon, Security Director at The Marin Hospital of Hendaye. "It is the only solution that can equip more than 1,500 doors with quick and wireless installation.” Intelligent eCLIQ key An eCLIQ solution gives managers control over important aspects of hospital security An eCLIQ solution gives managers control over important aspects of hospital security. They can issue access tailored to an individual’s needs and level of authority and amend it whenever required. External service providers use an intelligent eCLIQ key which automatically expires after a pre-defined period. This is much safer than relying on a contractor to return their mechanical key every time. Security, comfort, and flexibility Employees enjoy much greater comfort and convenience: Carrying a single eCLIQ key programmed with their permissions makes bulky key bunches a distant memory. “The Marin Hospital of Hendaye has gained in security, comfort, and flexibility. Employees hold only one key compared to 5 or 6 keys before,” adds Yves Bourdon. The rollout is ongoing, with another 500 eCLIQ cylinders already ordered and ready to install. The eCLIQ programmable key solution The eCLIQ cylinder range can bring almost any opening into an electronic access control system A fully electronic extension of ASSA ABLOY’s award-winning CLIQ® access control technology, eCLIQ is built around precision-engineered locking cylinders and high-end microelectronics. A standard battery inside each programmable electronic key powers the cylinder or padlock on insertion and encrypts the data transfer between lock, key, and system. The eCLIQ cylinder range can bring almost any opening into an electronic access control system. Robust, durable eCLIQ cylinder locks secure lifts, machines, mailboxes, cabinets, and more with the same control as sensitive doors. Programmable, wire-free access control “Like many hospitals around Europe, The Marin Hospital of Hendaye now relies on programmable, wire-free access control which is backed by decades of ASSA ABLOY investment and innovation in lock and key technologies,” says Tatiana Bezie, Sales Manager at ASSA ABLOY Opening Solutions France. “Organisations equipped with eCLIQ intelligent key-based access control can have confidence that their premises and employees are secure.”


Round table discussion
As the new year dawns, it's a good time for the security industry to look ahead to 2024. We asked this week's Expert Panel Roundtable: What will be the biggest surprise for security in the year ahead?
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Products


White papers

Physical access control
Download
Verkada workplace safety survey
Download
Securing care closer to patients
Download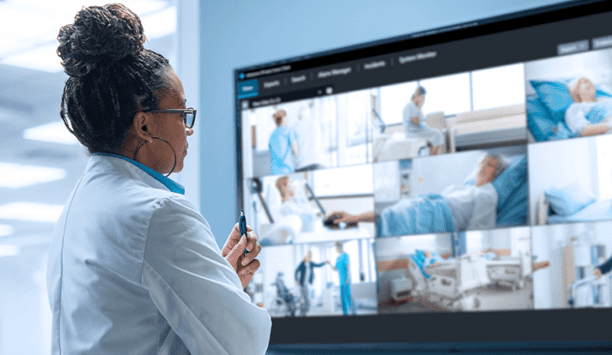
Essential data security strategies for healthcare
Download
Video technology strategies for hospitals are moving beyond security
Download
The future of healthcare security is connectivity
Download
Creating a secure and positive healthcare experience
Download
Integrated access control: reap the benefits of connected security
Download
Solve access control challenges in the healthcare sector
Download
The healthy market for video surveillance at medical facilities
Download

Videos
Hospital security: Manufacturers & Suppliers

Artificial Intelligence in Security
Download
Elevating security through multi-sensing solutions and large-scale AI
Download
Open credential standards and the impact on physical access control
Download
Combining security and networking technologies for a unified solution
Download
What is a universal RFID reader?
Download











































