Mercury Security, part of HID Global - Experts & Thought Leaders
White papers from Mercury Security, part of HID Global
Three reasons for adopting open architecture access control solutions
DownloadLatest Mercury Security, part of HID Global news & announcements
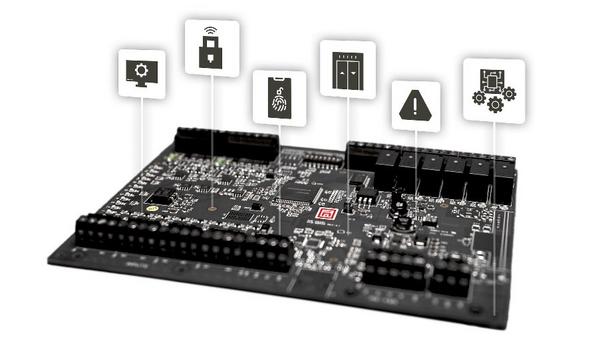
Mercury Security, the pioneer in open architecture access control hardware, is launching a new addition to its industry-defining controller platform—the Mercury embedded application environment, an open platform that enables technology partners and OEMs to develop and deploy custom applications directly on Mercury MP Controllers. “We have a lot of exciting things happening at Mercury,” said Steve Lucas, vice president of sales at Mercury Security. “We are excited to show customers the Mercury embedded application environment running on Mercury MP Intelligent Controllers, along with a range of new solutions targeting the platform. We’re giving our partners the ability to develop directly on the controller, unlocking new levels of system intelligence at the edge.” Traditional access controllers Unlike traditional access controllers that rely on server-based logic and are limited in upstream system connections, this platform brings real-time logic processing to the edge—reducing latency, increasing availability and enhancing system redundancy. By shifting intelligence closer to the door, the platform improves system responsiveness, minimises network dependency and enables advanced operational features. It also simplifies interoperability, seamlessly integrating controllers, IoT devices, elevators, readers, locks and more. Access control and IoT ecosystem Mercury embedded application environment delivers unmatched flexibility For access control and IoT ecosystem stakeholders who need a secure, scalable and customisable platform, the Mercury embedded application environment delivers unmatched flexibility—supporting third-party app integration and enabling custom business logic to run directly on the controller. Instead of just linking a reader to a management system for access decisions, Mercury controllers act as a nexus, integrating multiple systems and devices for broader functionality and stronger performance. Intelligent security systems “The access control industry is shifting toward more decentralised, intelligent security systems,” said Daniel Gundlach, vice president, head of Physical Access Control Solutions business unit in North America at HID. “Our embedded application environment gives our partners the tools to build smarter, more adaptable solutions that align with today’s challenges and tomorrow’s opportunities.” Key launch partners and apps Mercury is showcasing the broad capabilities of its embedded application environment in collaboration with key launch partners and their certified apps: ASSA ABLOY HES KS210 OSDP Access Control Server Cabinet Lock: With the Mercury KS210 device app, OEMs can now quickly & easily add support for up to 32 KS210 OSDP server cabinet locks without the need to build custom integrations. HID pivCLASS: Enables pivCLASS support on Mercury MP Intelligent Controllers, adding PKI-based authentication at the door to meet security standards required in government facilities and other regulated industries. SecuriThings: This system-class app simplifies security audits by discovering devices on the network and generating detailed reports on their status, including firmware versions, host connectivity and other key security metrics. Viakoo: This SaaS application maintains system health across CPS environments, such as physical security. System reliability is ensured with real-time monitoring, vulnerability identification, lifecycle data, and other critical details. Viakoo takes action to remediate vulnerabilities with firmware updates, password rotations, and certificate management. New standard in access control Mercury MP Controllers quickly set a new standard in access control, offering unprecedented flexibility Launched in June 2024, Mercury MP Controllers quickly set a new standard in access control, offering unprecedented flexibility. These controllers are the foundation for the Mercury embedded application environment, enabling software providers and integrators to seamlessly combine access control technologies, elevator control, building automation, IoT applications and third-party solutions into a unified, centralised infrastructure. This flexible approach eliminates vendor lock-in and provides the freedom to choose the right solution for specific customer requirements while future-proofing investments. OEMs and integrators Mercury Security, an HID company, has pioneered flexible hardware solutions that empower OEMs and integrators to create best-in-class systems for over 30 years. Mercury MP Controllers support a wide range of consistent standards, including OSDP, MQTT and TLS, ensuring interoperability across access control, building automation and IoT applications. The Mercury embedded application environment is available for developers now.
Mercury Security, the manufacturer of OEM technology, and HID, a pioneer in trusted identity and access control solutions, announce the next-generation Mercury MP Controllers, designed to deliver enhanced flexibility and security for businesses of all sizes. As technology advances, access control systems require robust encryption and advanced threat detection. Mercury MP Controllers The new Mercury MP Controllers empower access control software providers and integrators to seamlessly combine a wide range of access control technologies, elevator control, building automation, IoT applications, and third-party solutions into a unified, centralised, and fully robust infrastructure. This open approach provides the freedom to choose the right solution for specific customer requirements. Advanced safety features The new intelligent controllers were designed with advanced security features to safeguard sensitive data Taking this commitment a step further, the new intelligent controllers were designed with advanced security features to safeguard sensitive data and to help protect against evolving cyber threats. A robust cryptographic engine supported by a secure boot CPU, crypto chip, and data encryption aims to provide proactive protection against unauthorised access and attacks. Robust, future-ready access control “In today's dynamic business environment, organisations demand access control solutions that are not only secure and reliable but also flexible enough to adapt to evolving needs,” says Steve Lucas VP of OEM Sales at Mercury Security. “The new MPControllers deliver on these critical requirements, empowering businesses to create robust, future-ready access control systems with increased ROI, scalability, and cybersecurity at their core.” Benefits of controllers The Mercury MP Controllers provide partners and end users with: Flexibility: The freedom to design and upgrade systems without limiting software and hardware choices, and seamlessly integrate the latest technologies with no costly rip-and-replace projects. This flexibility extends to OEMs, allowing them to seamlessly integrate the controllers with both on-premises and cloud-based access control environments. Scalability: The ability to meet system architecture from a single door to an entire enterprise. Heightened Security: The support for physical and cybersecurity features to help keep networks and data safe. Reliability: The peace of mind of having invested in reliable and trusted hardware in the business. Dual-footprint circuit design The Mercury MP Controllers deliver powerful new features such as a dual-footprint circuit design with alternate components for business continuity, a future-ready development environment for expanded integrations, and the adoption of enhanced cybersecurity best practices, like ARM TrustZone, to protect systems. The MP controllers will be available later in 2024 through Mercury OEM partners.
Mercury Security, the manufacturer of OEM technology, and HID, a pioneer in trusted identity and access control solutions, announce the next-generation Mercury MP Controllers, designed to deliver enhanced flexibility and security for businesses of all sizes. Mercury MP Controllers As technology advances, access control systems require robust encryption and advanced threat detection. The new Mercury MP Controllers empower access control software providers and integrators to seamlessly combine a wide range of access control technologies, elevator control, building automation, IoT applications, and third-party solutions into a unified, centralised, and fully robust infrastructure. This open approach provides the freedom to choose the right solution for specific customer requirements. Advanced security features A robust cryptographic engine supported by a secure boot CPU, crypto chip, and data encryption Taking this commitment a step further, the new intelligent controllers were designed with advanced security features to safeguard sensitive data and to help protect against evolving cyber threats. A robust cryptographic engine supported by a secure boot CPU, crypto chip, and data encryption aims to provide proactive protection against unauthorised access and attacks. Future-ready access control systems “In today's dynamic business environment, organisations demand access control solutions that are not only secure and reliable but also flexible enough to adapt to evolving needs,” says Steve Lucas VP of OEM Sales at Mercury Security. “The new MP Controllers deliver on these critical requirements, empowering businesses to create robust, future-ready access control systems with increased ROI, scalability, and cybersecurity at their core.” MP controller benefits The Mercury MP Controllers provide partners and end users with: Flexibility: The freedom to design and upgrade systems without limiting software and hardware choices, and seamlessly integrate the latest technologies with no costly rip-and-replace projects. This flexibility extends to OEMs, allowing them to seamlessly integrate the controllers with both on-premises and cloud-based access control environments. Scalability: The ability to meet system architecture from a single door to an entire enterprise. Heightened Security: The support for physical and cybersecurity features to help keep networks and data safe. Reliability: The peace of mind of having invested in reliable and trusted hardware in the business. New features The Mercury MP Controllers deliver powerful new features such as a dual-footprint circuit design with alternate components for business continuity, a future-ready app development environment for expanded integrations, and the adoption of enhanced cybersecurity best practices, like ARM TrustZone, to protect systems. The MP controllers will be available later in 2024 through Mercury OEM partners.
Insights & Opinions from thought leaders at Mercury Security, part of HID Global
You’re no psychic. You probably don’t have the power of clairvoyance. But guess what? When it comes to your security, none of that matters. You can still create future-proof security by properly equipping yourself. Here’s how. Understanding access control Security is changing faster than ever before. With new threats inside the workplace and smaller security teams taking on more tasks, IT and security personnel must automate their processes using new technology. One difficult aspect, however, is choosing the right technology. By analysing technological trends and assessing your current and future needs, you can preemptively find solutions. Ultimately, in the long run, these solutions will save you time and expense. Ultimately, in the long run, these solutions will save you time and expense But how do you distinguish a momentary trend from a long-term solution? Do you really need to pay extra money for that feature, or will you stop using it in a year? To properly invest in future-proof access control, IT and security teams must look at three different aspects of technology: Flexibility, Scalability, and Efficiency. Access control system Flexibility: Hardware It’s not the sexiest thing to talk about, but hardware is crucial to any security system. Readers, locks and controllers are the backbone of any access control system, and choosing the right hardware is essential when it comes to planning for the future. Broadly speaking, hardware falls into two categories: proprietary and non-proprietary. For those teams considering a new installation, choosing between proprietary access control and non-proprietary access control is a decision that will affect your organisation over the long term. Long-term unseen expenses Proprietary Hardware Pros: Upfront costs can be less expensive; One vendor for hardware and software. Cons: Locked into one vendor; Long-term unseen expenses. Imagine buying a microwave that only cooked foods produced by the microwave manufacturer Imagine buying a microwave that only cooked foods produced by the microwave manufacturer. In a booming economy, the manufacturer produces all sorts of tasty treats—popcorn, lasagna, pies. But when the economy takes a dip, the manufacturer scales back its production and announces it will only sell liver and onions. Now maybe you’re a liver and onions fan, but on the off chance you like variety in your diet, this would be a problem. Your microwave has been rendered useless and has essentially become a liver and onions cooking machine. Potential system vulnerabilities Like the microwave example, proprietary hardware leaves companies at the mercy of the manufacturer. If the manufacturer goes out of business, the system will cease to function, and customer support will be non-existent. Consequently, your security team will likely have to install an entirely new hardware system. Costly, right? Let’s consider a less dramatic scenario. What if a manufacturer, instead of closing, decides to scale back its operations? It provides less frequent updates and fewer new feature releases. Without these updates, your security becomes more vulnerable and outdated. In the long run, choosing proprietary hardware can end up costing teams a lot more than they are saving and expose potential system vulnerabilities. Non-proprietary hardware Pros: Free to switch software vendors; Long-term system flexibility. Cons: Upfront costs can be more expensive. Non-proprietary hardware gives teams the power to switch software providers at any point Where proprietary hardware fails, non-proprietary thrives. The most important aspect of a non-proprietary system is the flexibility it grants. Non-proprietary hardware gives teams the power to switch software providers at any point, without replacing the hardware. In the aforementioned microwave scenario, the customer was relegated to a life of liver and onions because of their proprietary microwave. However, had they chosen a non-proprietary microwave, then they could have eaten any meal. They wouldn’t be limited to the food options sold by the manufacturer. Non-proprietary hardware also accounts for much of the current marketplace. If your team currently uses non-proprietary hardware—Mercury Security, HID, Wavelynx, or STid-- but is considering switching to a cloud-based provider, then something called a software takeover could be useful. A software takeover is a process by which a new software provider replaces a former one, though no new hardware is installed. Scalability: on-prem or the cloud? Whether working for an enterprise, hospital or school district there is always potential for expansion. As an organisation grows or shrinks, so must its access control. At your latest ‘all-hands’ meeting, the CEO announces that you will be aggressively expanding At your latest ‘all-hands’ meeting, the CEO announces that you will be aggressively expanding. They want security to be up and running in three new countries by the end of the quarter. Luckily, you have just finished migrating from on-premises access control to the cloud. You handle scaling the operation with relative ease. IT and security teams must choose between cloud access control and legacy on-premises equipment. The greatest determination of scalability lies with the server. Cloud-based access control Pros: Easily scalable; Less regular maintenance; More secure; Integrations; Centralised storage. Cons: On-going subscription costs; Migrating from on-premises access control. When asked about the trends shaping the near future of access control, 38% of respondents said cloud hosting would be an important feature. Though this was a lower percentage compared to the responses at the beginning of Covid-19 (50% mentioned cloud), cloud security is poised to grow by as much as 13.7% each year. Connecting software stacks Here are some facts about cloud-based access control: Security: In the past, what held the cloud back were concerns about cyber security. But advances in security, including 256-bit encryption for data at rest and data in transit, have significantly improved the cloud. Integrations: Talk to any IT director who has already made the migration from on-prem to cloud, and they’ll mention ‘integrations.’ The cloud gives administrators the ability to more quickly connect their software stacks. Some popular integrations include visitor, video, identity, and notification management. Though integrating on-premises access control is possible, it takes significantly longer and is more costly than integrating with the cloud. Remote Access: Since COVID-19, IT and security professionals have been searching for remote ways to work. However, remotely connecting to an on-premises access control system often requires a VPN. The cloud allows teams to work remotely and access any of the buildings in their portfolio while off site. Physical access control Efficiency: Software Features Another important aspect of physical access control is its software features Another important aspect of physical access control is its software features. While the needs vary from industry to industry, some overlap exists. For instance, a global dashboard can give oversight across buildings on college campuses or offices of a national enterprise. A security team in New York can monitor the access events or provision a new employee in Tokyo. Broadly speaking, IT and security teams are looking for software that boosts day-to-day efficiency and is customisable. These features include: Custom Reports- Spreadsheets or PDFs that give you an aggregated view of access events that have occurred over a given period. Custom Roles- Administrators the ability to create an organisational framework by access permissions. Badges- Create branded physical or digital badges according to permission level. Emergency Add-ons- Custom door plans and Muster reporting can help in crisis situations. For example, if there is an active shooter, certain doors can be left open or locked automatically to prevent the shooter from gaining access to certain areas. Cloud access control has made it easier to implement new features. Ultimately, the cloud gives IT and security administrators more power to quickly request and deploy the features they find most worthwhile. Final thoughts on security With the rapid technological transformation brought about by cloud and mobile access control, it’s important that IT and security teams stay ahead of the curve. In order to decide which system is the right choice for you, it’s important to evaluate not only your current but also future needs. Creating a checklist of the most important features and deciding whether to host all the server yourself are two important steps to pinpointing the perfect access control system. For more information, ask access control providers for a free demo.
Open Options, based in Addison, Texas, provides a truly open access control architecture that will strengthen the ACRE portfolio and increase the breadth of solutions offered by the global provider of security systems. The acquisition of Open Options is also an opportunity for ACRE to focus on growth opportunities in North America and “balance the scales a bit,” says Joe Grillo, CEO of ACRE, which significantly grew its reach in Europe, the Middle East and Africa with the acquisition of Siemens Security Products in 2015. “Open Options is also a company that's growing, is profitable and fits seamlessly into our vision for the access control space in which we operate,” says Grillo. Independent operations The strength of Open Options in the Southwest provides significant additional coverage for ACRE in that region of the United States The Open Options brand will continue to operate independently under the ACRE umbrella. Open Options CEO and Founder Steve Fisher will continue in his role as leader of the company, says Grillo. “There is a strong and competent management team in place that will continue to provide leadership going forward.” Open Options’ open-architecture access control solutions will add value to the solutions ACRE already offers under the Vanderbilt brand. In a market that has traditionally been proprietary, the open-platform solution offered by Open Options helps deliver more opportunity to offer customers a full-scale solution based on their needs, says Grillo. In addition, due to its origin as a Texas-based company, the strength of Open Options in the Southwest provides significant additional coverage for ACRE in that region of the United States. Technical and financial resources On the other hand, ACRE provides a greater level of technical and financial resources that Open Options can utilise to help them grow even faster. These resources were not as available to the company if it remained independent, Grillo notes. ACRE’s divestiture of Mercury Security in 2017 facilitated this investment. As discussions began earlier this year, ACRE realised the potential of adding to its access control portfolio in the North American market, says Grillo. Open Options and Mercury have been "partners" for 20 years; Mercury provides hardware panels for Open Options systems. Each company will manage and make decisions about their reseller channels independently “The Mercury brand continues to be a strong one, so we're interested in continuing to nurture that relationship, and in fact we have become a larger and stronger partner to Mercury as ACRE,” says Grillo. “After owning Mercury for a number of years, we had the understanding of the company, the product portfolio and the partner relationships that defined it, so we were confident that the deal would be a positive one for the ACRE brand.” Meeting customer needs “Open Options and Vanderbilt share some customers already and we can leverage that by gaining more share of their business while providing them with a portfolio that will meet a broader set of customer needs,” says Grillo. “Where possible, we can look for synergies in channel partners that are not currently shared to provide access to both brands. This will be a benefit to Open Options, Vanderbilt and our customer base. However, importantly, each company will manage and make decisions about their reseller channels independently.” Are there more acquisitions on the horizon for ACRE? “We're always looking for opportunities that fit into the nature of our business,” says Grillo. “Companies that have growth potential and share similar go-to-market strategies and visions for the future are of particular interest to ACRE. "We're still operating in a highly fragmented market, so we're going to see continued consolidation in both access control and beyond, which means ACRE will be looking for the right opportunities to follow along that path.”
One of the biggest recent security divestitures in the news was the sale of Mercury Security to HID Global, which occurred around a year ago. The seller in that transaction was ACRE (Access Control Related Enterprises), also the parent company of Vanderbilt and ComNet. We recently spoke to founder and CEO Joe Grillo, a 30-year industry veteran, about the mergers and acquisitions (M&A) market, ACRE’s future, and new opportunities opened up by the Mercury sale. Q: What’s new with ACRE? Grillo: We have an opportunity to have organic growth and to have some scale on a global basis to be a decent size player" ACRE is a company I founded in 2012, and since then we have had six acquisitions and one divestiture. We’ll never focus on ACRE as a brand, but we currently have more visibility of ACRE as a parent company with our two strong brands, ComNet and Vanderbilt. Last year was a very busy year [with the sale of Mercury Security to HID Global] because it takes as long to sell a brand as to buy one, maybe more so. Q: What’s next? Grillo: What you are seeing from us this year is that we are again in a buying mode. No announcement yet, but we expect one by the end of the year. We are well-funded, have great partners, and see an opportunity to continue to grow acquisitively as our highly fragmented space of access control continues to consolidate. From the standpoint of ACRE, with the ComNet and Vanderbilt brands, we are also doing more integration on the backside – not what the customer sees. We will continue to grow toward a $200 million business. We were there when we owned Mercury, and we will get there again. We have an opportunity to have organic growth and to have some scale on a global basis to be a decent size player. Because ACRE are owned by a private equity company, we are brought into every opportunity: ComNet is a good example" Q: Do you see the M&A market being more competitive – more companies looking to acquire? Grillo: There’s a lot of money chasing not-so-many deals, so evaluations can get expanded. But as interest rates creep up, it is definitely a challenge to find the right valuation, the right financing and the right strategic fit. It is a very strategic market. Q: There have been some big acquisitions lately. Were you guys involved at all in evaluating those opportunities? Grillo: Because we are owned by a private equity company, we are brought into every opportunity. An example of that was ComNet. I would not have been aware that the founder passed away two years ago and that there was this opportunity to own the business. So we look at everything; anything that’s out there we look at. The biggest recent announcement in our world was S2 (being sold to UTC/Lenel), and, yeah, we looked at that. It didn’t fit our profile – it was too expensive. Great business, and it’ll be interesting to see how it fits into the UTC environment. There was also Isonas [which was recently sold to Allegion], but the size didn’t add enough scale, but I like the technology. ComNet sells communication networking solutions and products, which is more attractive than video systems for ACRE Q: So what are you looking for in an acquisition? Grillo: It’s hard for us to find something that moves the needle, and you have to find that right balance. Is it something we can digest and have the financing for, and also is there room on the back end? We are private equity-owned, so we know there will be an exit for our investors, too. So we have to find the right balance, good valuations, the right size and digestible. If you look at our acquisitions, we have done two “carve outs.” The Vanderbilt name didn’t exist until we bought the business from Ingersoll Rand, and then we bought the [intruder] business from Siemens. That’s how Vanderbilt came about. You get a lot of value when you carve out a business, but there’s a lot of work. In the case of Mercury or Access Control Technology (ACT) that we acquired; they were growing and profitable but they stretch your finances a lot more. So you have to find the right mix in there. Q: Does video interest ACRE at all? Grillo: We have to find the right balance, good valuations, the right size and digestible"ComNet is our video play. ComNet sells communication networking solutions and products, and 70 to 80 percent of that is used for video systems. But unlike cameras, which don’t interest us, it’s actually good margins, highly specialised repeat business and with good channel partners. So where are we going to play? Cameras – no (because of commoditisation). We have some recorder technology (from the Siemens acquisition) and we have the communication networking technology (with ComNet). On the software side, we have looked at a lot of the VMS companies, and a lot of them have been on the market. But the valuation expectations can be high because they are software companies. And we really believe in partnering as a good thing, too. If we integrate to Milestone or Salient or some of these companies, we will never lose an access control client because they chose a particular VMS. Q: ACRE is also looking to grow organically, isn’t it? Grillo: From a technology perspective, we are a product company and we are continuing to bring new products to the market with the ComNet communication networking business and the access control business. And in Europe, we have a third leg of the stool, which is the very successful intrusion and burgular alarm business we acquired from Siemens (SPC products now sold under the Vanderbilt brand). That business continues to do well and is now one of the highest performing segments in our portfolio.The intrusion and burgular alarm continues to do well and is now one of the highest performing segments in our portfolio" Q: But you don’t have to own a company to make it part of your solution. Grillo: An important word is integration. We have to integrate to all the wireless locks. We have to integrate to the VMS systems. But we don’t have to own them. Q: How has the Mercury Security divestiture impacted the rest of your business? Grillo: It has opened up the opportunity for us to look at Mercury partners as possible acquisition targets without worrying about conflicts with the very good business of Mercury. We have more flexibility now compared to the Mercury era. Q: How will the economic cycle impact the security market? Grillo: Interest rates are a much bigger issue than the overall economic cycle. We talk a lot about it with our owners – clearly interest rates are tightening up. If you go out to do acquisitions or to borrow money to do something with your business, it will be tougher than it was two years ago, and it may get worse in the next two years. Security is less impacted by the economic cycle than some industries.
Artificial Intelligence in Security
DownloadElevating security through multi-sensing solutions and large-scale AI
DownloadOpen credential standards and the impact on physical access control
DownloadCombining security and networking technologies for a unified solution
DownloadWhat is a universal RFID reader?
DownloadMercury Security MR62e IP-enabled interface module
Mercury Security LP1501 PoE+ Edge-capable Intelligent Controller
Mercury Security LP1502 Intelligent Controller